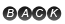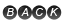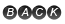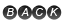There are various definitions of IoT, but to keep things simple we will say everything that can be “connected” will be connected. IoT promises an ecosystem where devices used in day to day activities will not only be connected but sharing, analyzing and implementing actions on their own. There are varying forecasts for how big the IoT opportunity is. Whether those forecasts are right or wrong, IoT will be a major part of future business and home life. However, the journey will not be without challenges and road-blocks.
Most of the challenges like standardization, wide-scale deployments and changes to organizational structures resulting from the implementation of IoT solutions, will be resolved over time. There is one road block that will likely prove more troublesome IoT privacy and security. And it is one that has its own evolution and will likely grow at twice the speed of the IoT industry.
Security: difference between IoT and PC/ Laptop/ Mobile
In the case of computers, updates come directly from the operating system provider, the application owner or hardware vendor. Hence the consumer user can apply each update separately and within an appropriate timeframe. However, IoT device manufacturers will need to gather updates from chipset/module vendors, then apply their own updates on top to provide a viable solution for consumers. This complex process will require IoT manufacturers to take regular initiatives. Given the long potential life of some IoT devices, it is likely that sustaining support over long periods will be challenging.
Mirai: The latest attack on IoT security
- Mirai is a piece of malware designed to launch Distributed Denial of Service (DDoS) attacks and is the successor to qBot – a malware ‘worm’ that can propagate rapidly across multiple endpoints.
- Mirai has, so far, infected an estimated 40,000 IoT devices online and about 2.5 million IoT devices offline.
- The initial devices infected were Digital, Network Video Recorders, IP cameras and routers that effected devices connected to them and so forth.
- McAfee Labs estimates that 2.5 million Internet of Things (IoT) devices were infected by Mirai by the end of Q4 2016, with about five IoT device IP addresses added to Mirai botnets each minute at that time.
- Other variants of Mirai: BrickerBot (BrickerBot.1 and BrickerBot.2 BrickerBot.3), the botnet that permanently incapacitates poorly secured IoT devices with a much quicker number of 1295 attacks within 15 hours

There are various groups tackling these sorts of the security threats and there are, of course, sensible measures manufacturers and users can apply. Conventional approaches include:
- Tallinn Manual 2.0 on the International Law Applicable to Cyber Operations launched on 8th February 2017. The drafting of the Tallinn Manual was facilitated and led by the NATO Cooperative Cyber Defense Centre of Excellence.
- Cyber Threat Alliance: On February 13, the CEOs of the six founding members (Check Point, Cisco, Fortinet, Intel Security, Palo Alto Network and Symantec) of the Cyber Threat Alliance joined to announce the formal launching of the CTA as an independent governance structure.
- Nominum, a company that have written almost 90% of world’s DNS Code. It provides Nominum N2 Threat Avert, a layer of defense against Mirai.
- Securing IoT devices
- Disable unnecessary services or ports on these systems to reduce exposure to possible entry points of infection. Mirai exploits unused ports
- Connect IoT devices using secure Wi-Fi. Create strong passwords and use the latest security protocols, such as WPA2.
- Disable Universal Plug and Play (UPnP) support. Many IoT devices support UPnP, which makes the device discoverable on the Internet and vulnerable to malware infections.
- Power-cycle IoT devices periodically. Malware is commonly stored in a volatile memory and can be erased by shutting off and restarting the device.
There are also unconventional approaches – essentially fighting fire with fire. Unconventional Solution: Hajime is one such approach:
- Rumors suggest white hat hacker is responsible for the Hajime IoT botnet, which is on a mission to secure IoT devices vulnerable from the notorious Mirai malware.
- Both Hajime and Mirai have a similar self-propagation method, both infecting host devices, however their goals are opposite.
- Hajime is more complex than Mirai as it is controlled by peer-to-peer propagating commands through infected devices
- Hajime is not the first example of so-called vigilante malware. In 2015, a malware called “Wifatch” also targeted IoT devices and closed ports, changing default passwords and leaving behind warning messages.
Mirai Effected Map Overview (as on April 2017)

*Source: MalwareINT
The future of IoT: Privacy and Security
IoT devices will continue to be hacked and will be exploited for serious crimes in cyberspace. IoT malware currently uses default credentials to gain control of devices, the easiest path. Once that door closes, self-evolution will kick-in and attackers will find other entry points. IoT malware is currently basic, but in future we will surely see more professional and well-funded attackers. As a result, we can expect more advanced IoT bots. The probably attack vectors will include:
- Exploiting vulnerabilities in real-time operating systems, especially targeting industries that are solely dependent on IoT devices.
- More advanced bypassing mechanisms such as encrypted communication, peer networks, and more complex control structures.
However, with proper resources and collaboration between IoT security companies to bring their best solutions together as to create more concerted offerings that can not only fight back against these malwares and botnets but even learn and evolve on their own

*Source: Mc Afee, AV-TEST, Counterpoint